6. Supporting assets, impacts, scenarios
The reference lists are accessible through the Administration menu by the DPO and their team (assistants). They are fully customizable and can be enriched.

The reference frameworks are derived from the document "Knowledge Bases" by the CNIL:

 Data supporting assets
Data supporting assets
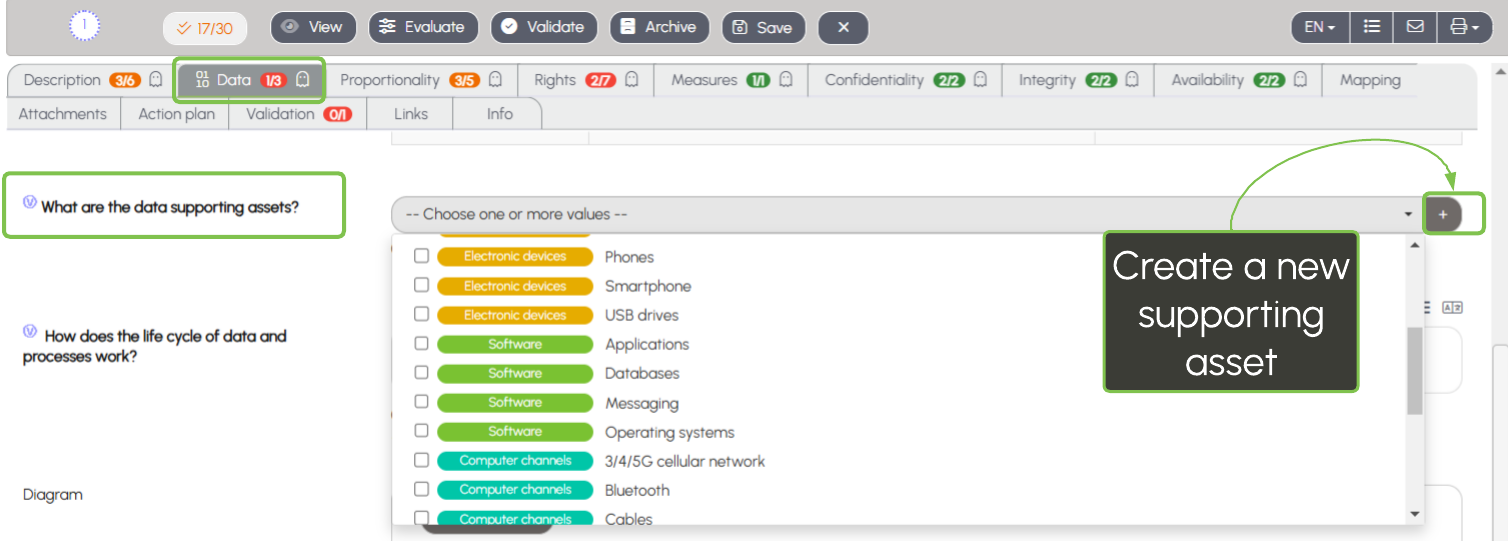
The supporting assets are organized by type and selected in the "Data" tab. Analysis authors can easily add new supporting assets:
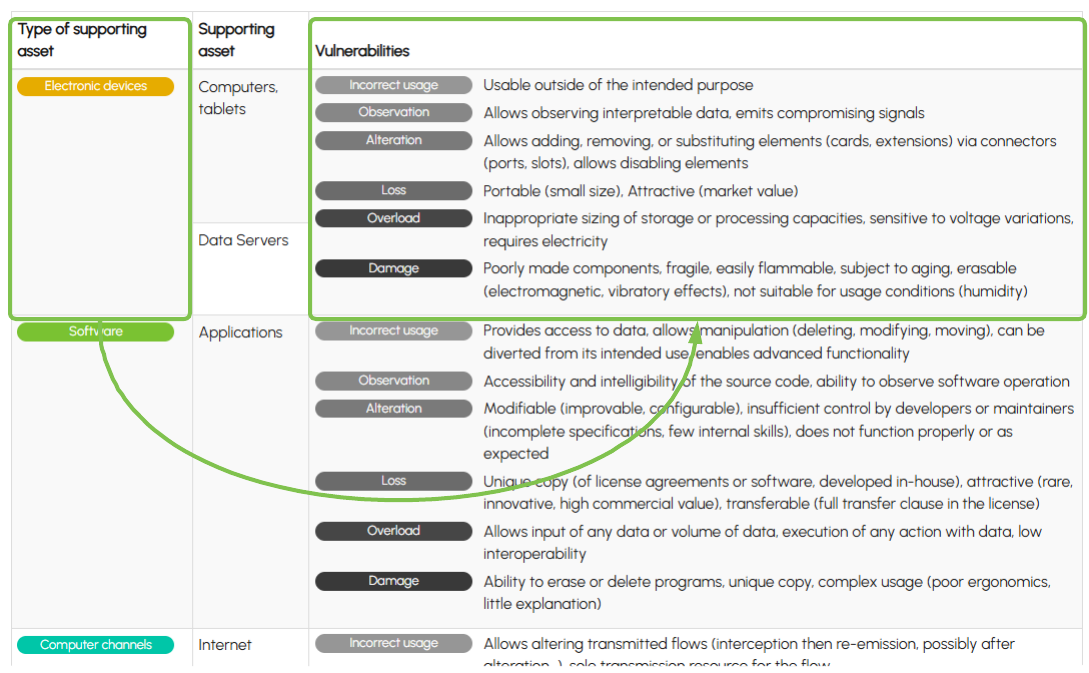
Once selected, the supporting assets are displayed in a summary, highlighting vulnerabilities by type to assist you in the analysis:
At the bottom of the "Measures" tab, you will find the list of selected supporting assets. You can identify supporting assets with residual vulnerabilities, based on the applied security measures, that require review. By default, all supporting assets are selected:
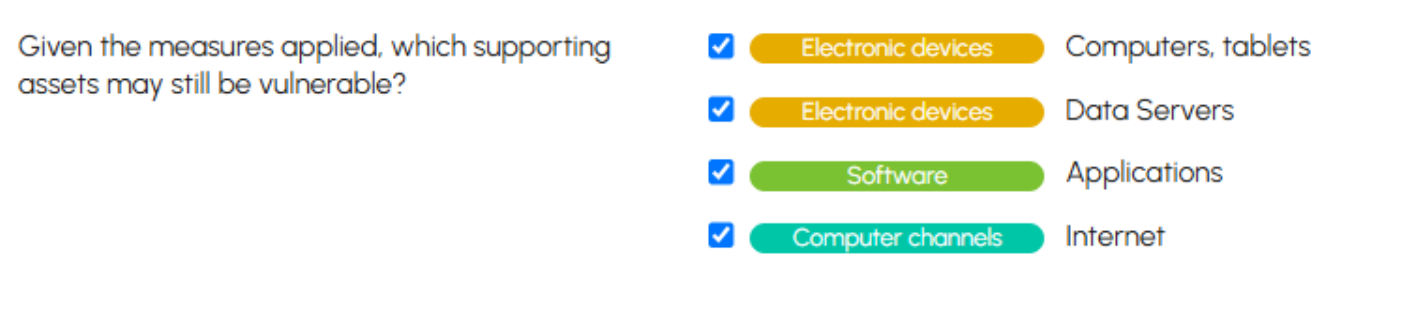
The supporting assets checked here will be used in the risk analysis to create scenarios.
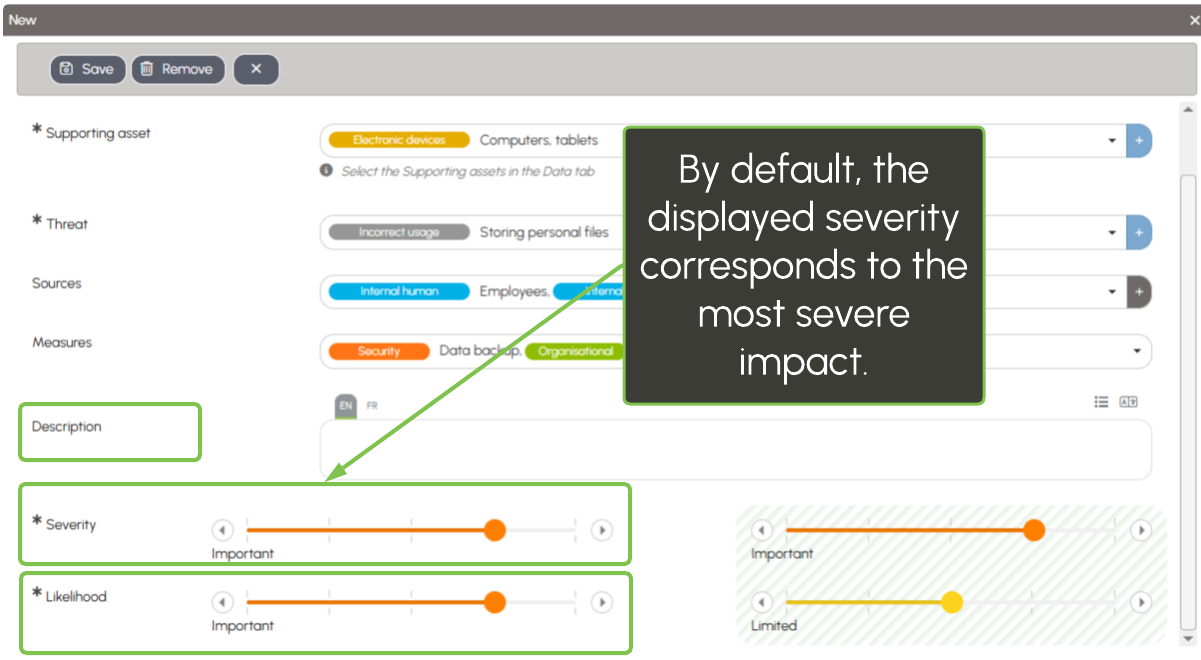
 Impacts on the data subjects
Impacts on the data subjects
Impacts are assessed for the three types of risks in the "Confidentiality," "Integrity," and "Availability" tabs.
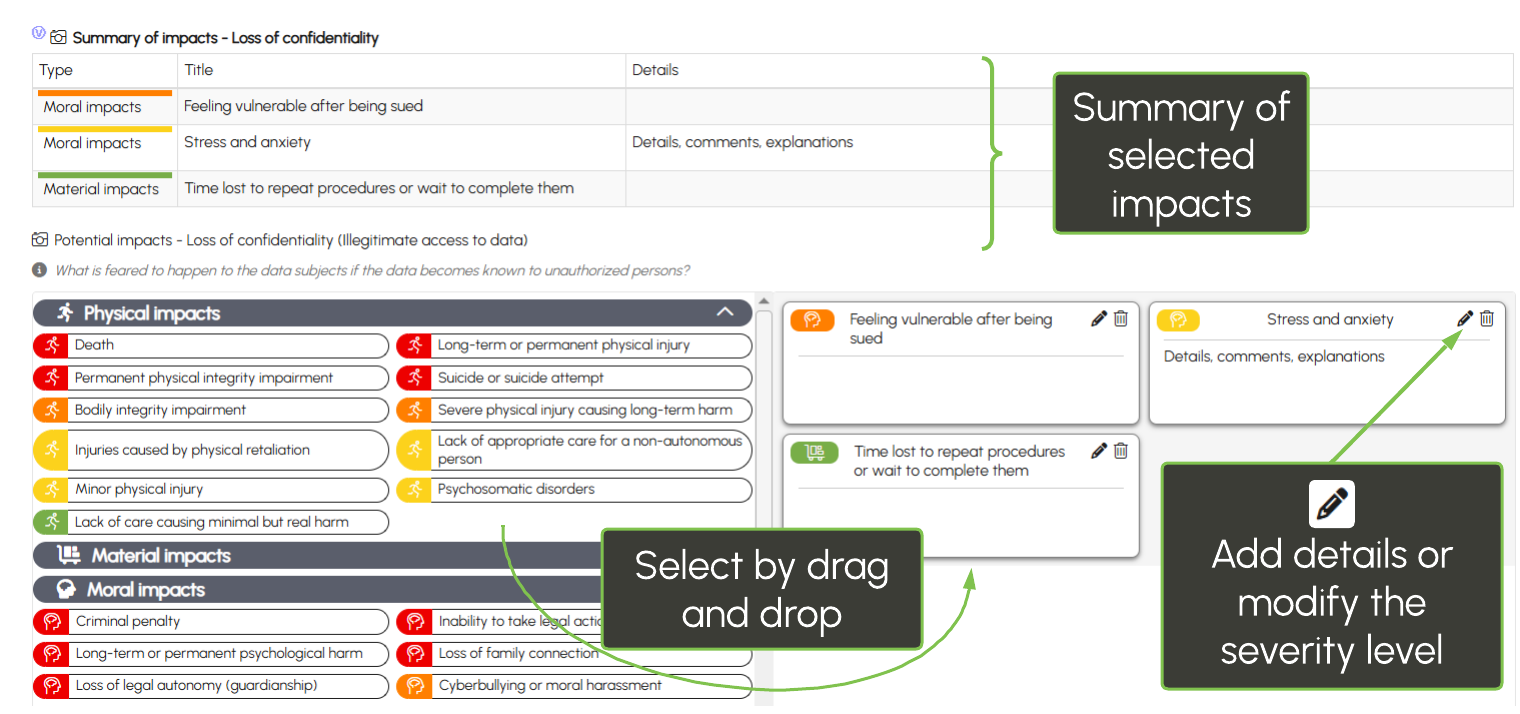
They can be physical, material, or moral and are associated with a severity level:

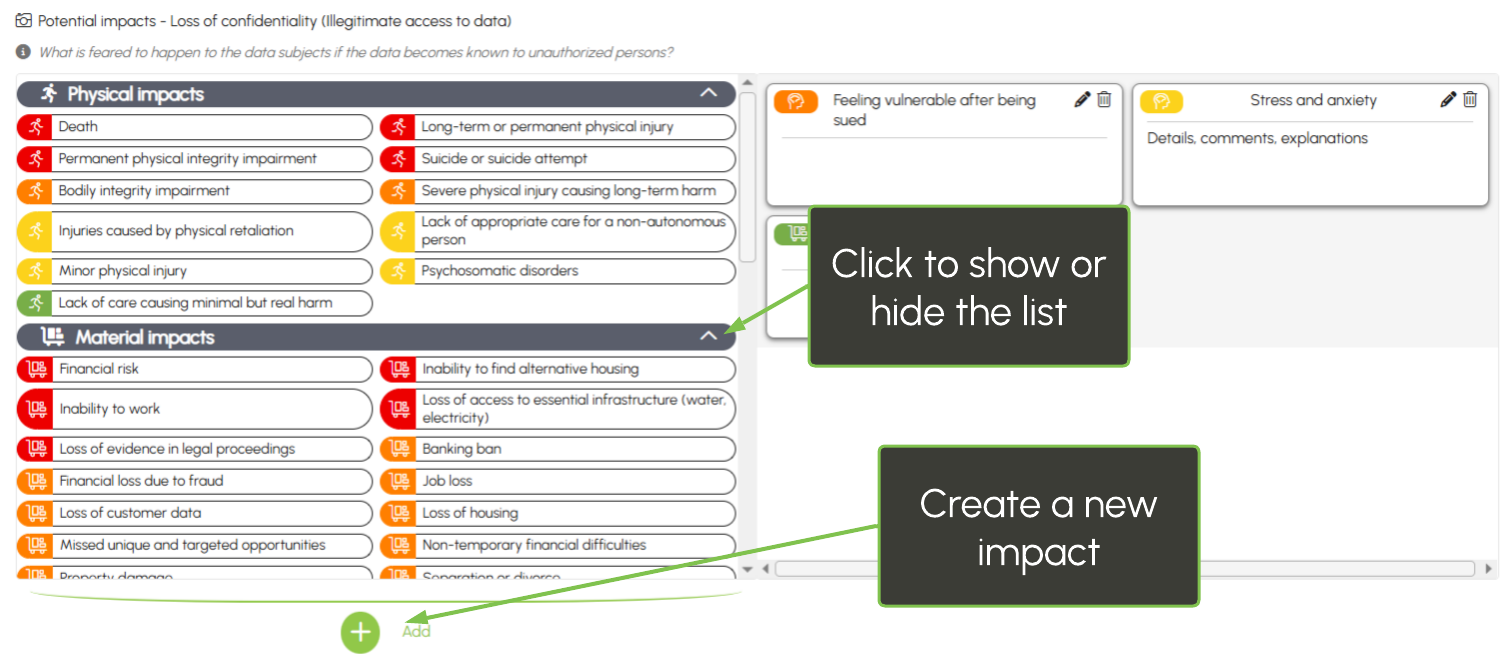
You can easily add new impacts at the bottom of the list:
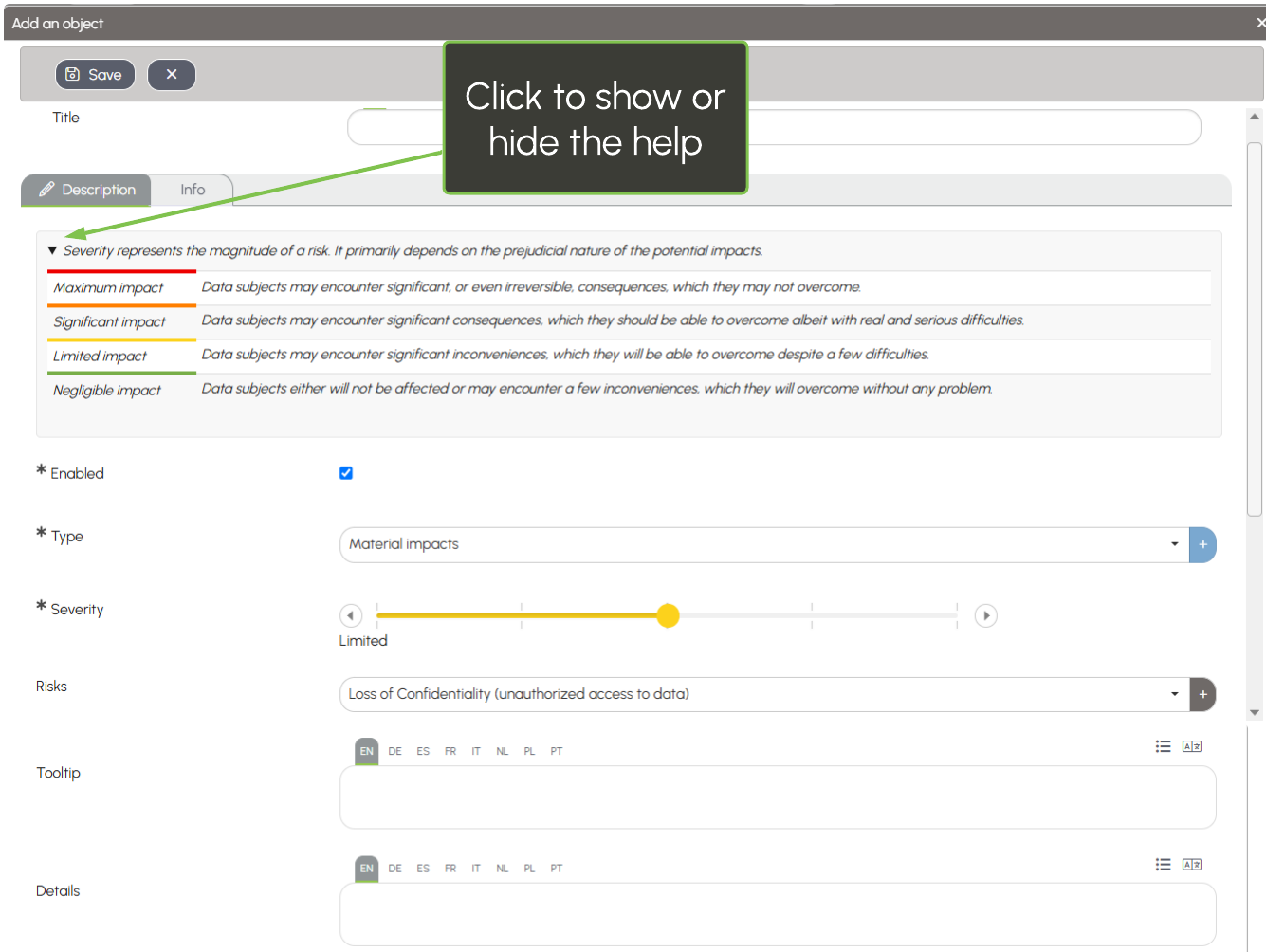
The definitions from the CNIL's PIA module assist you in determining the severity of impacts when creating them:
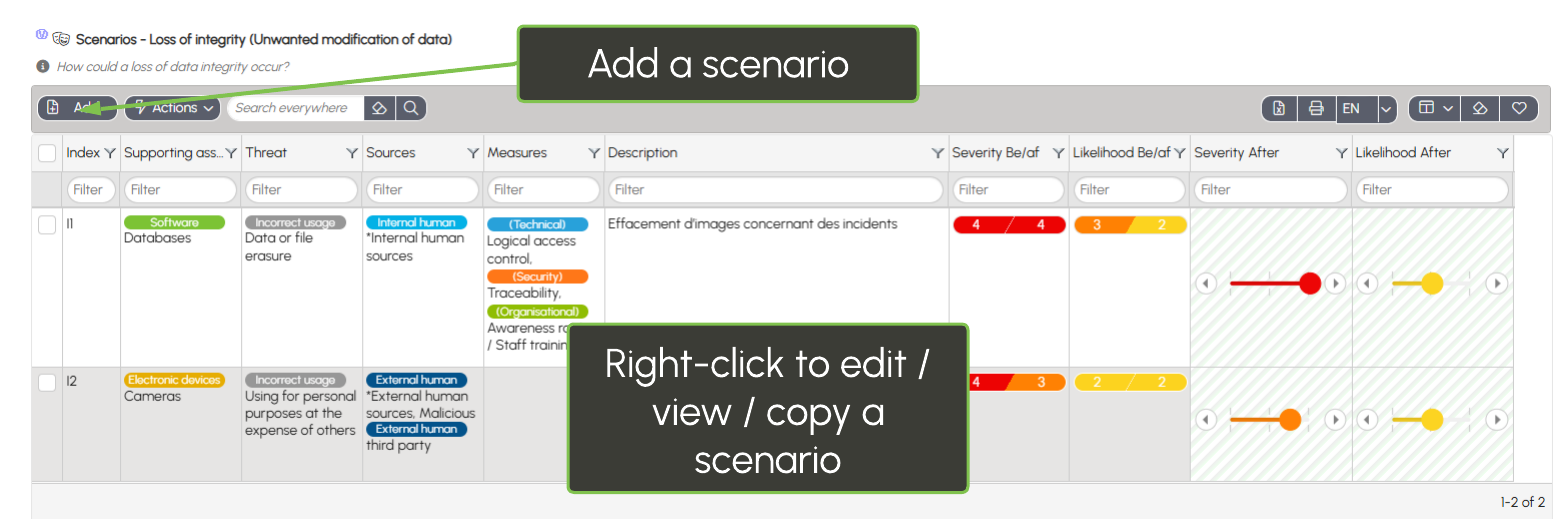
 Risk scenarios
Risk scenarios
For each type of risk (loss of confidentiality, integrity, or availability), you can build multiple scenarios:
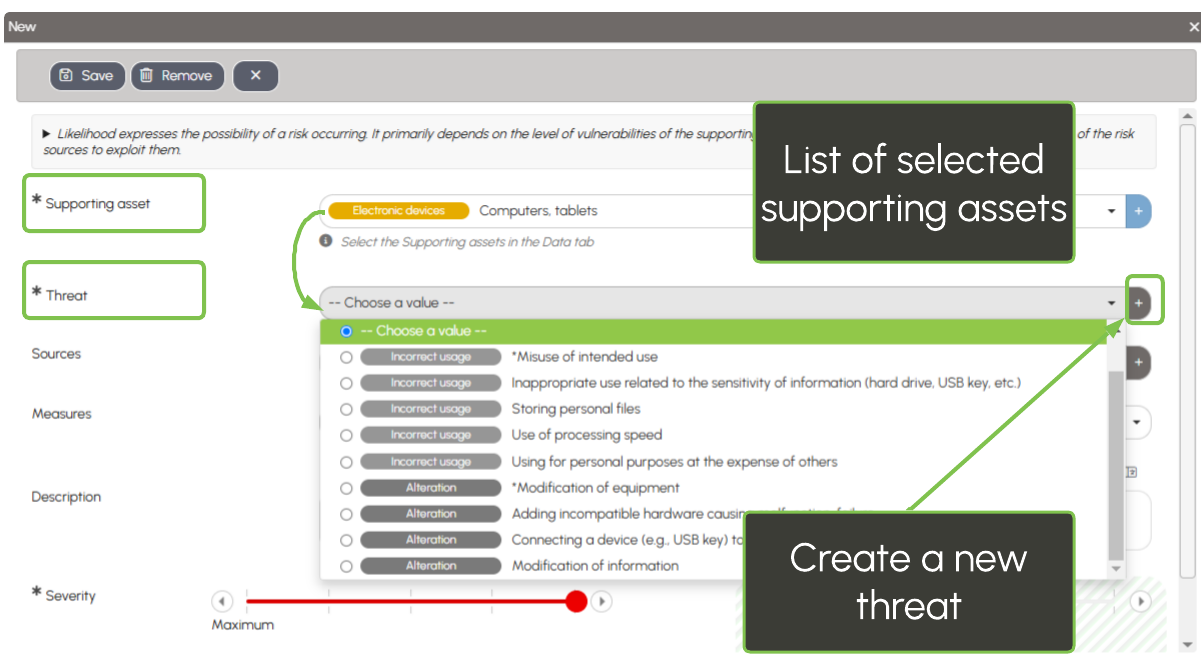
The suggested threats depend on the selected supporting asset and the type of risk, according to the lists from the CNIL's knowledge base. This allows you to examine the different possible threats for each supporting asset.
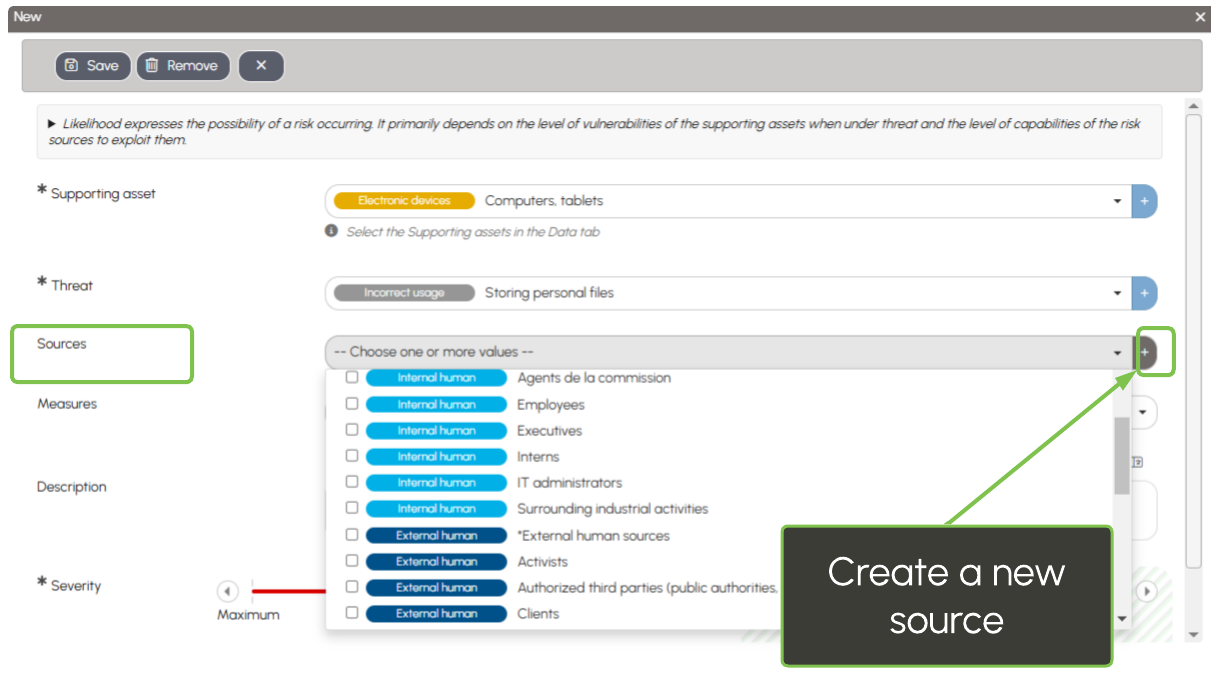
Threat sources are categorized into three types: internal human, external human, or non-human. From the Administration menu, the DPO can customize this list to match their organization.
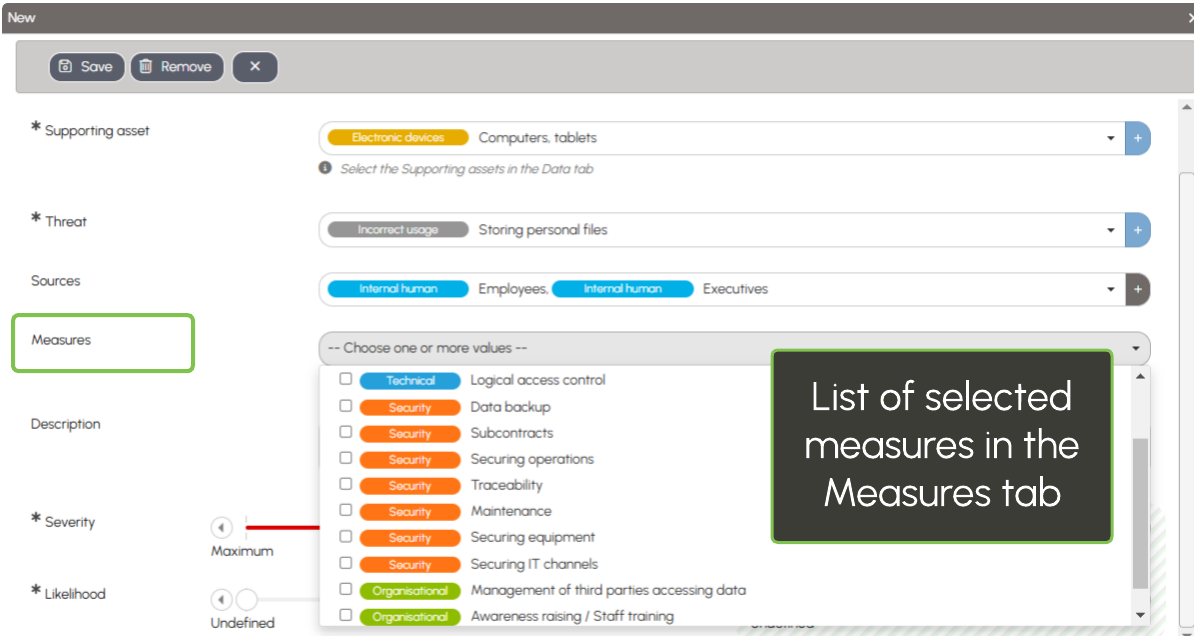
Select the measures to implement in order to reduce the risks:
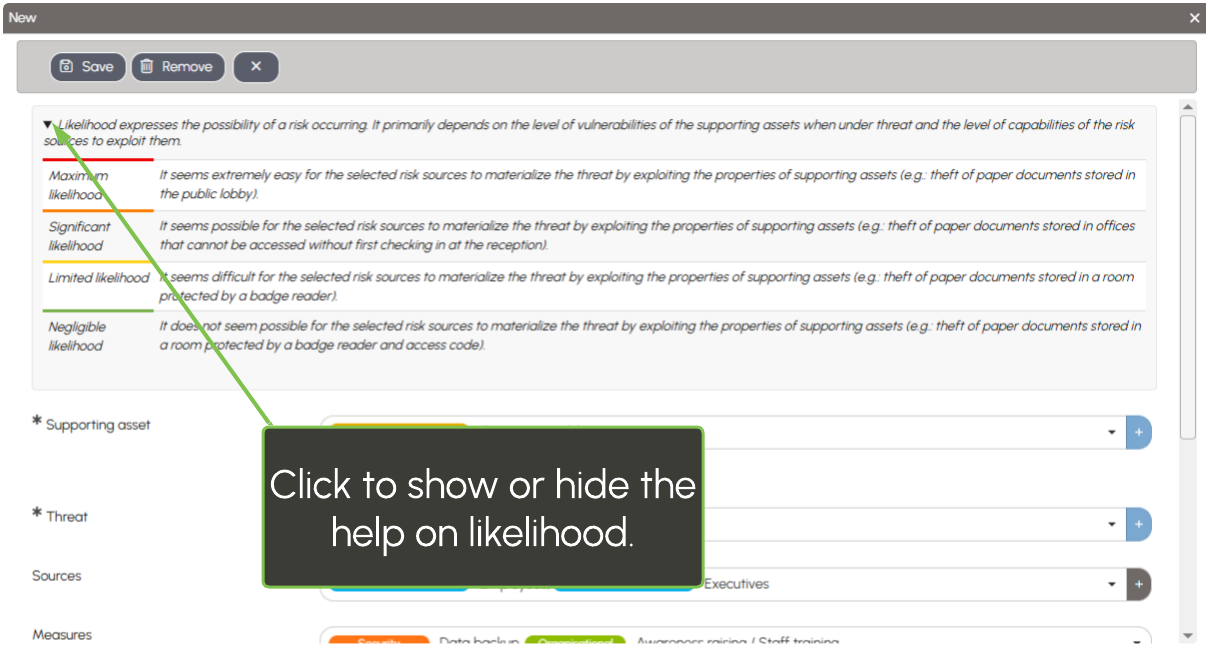
Add a description of the threat and assess its severity and likelihood. The evaluation of threats after applying the measures can be done directly from the list of scenarios.